A Deep Dive into Network Penetration Testing: Safeguarding the Digital Backbone
In today’s digitally interconnected world, the security of your organization’s network is paramount. With cyber threats constantly evolving in sophistication, it’s essential to identify and remediate vulnerabilities before malicious actors can exploit them. This is where network penetration testing comes into play. In this comprehensive guide, we will explore network penetration testing, its significance, methodologies, and the steps involved in securing your digital backbone.
Understanding Network Penetration Testing:
Network penetration testing, often referred to as “network pen testing” or “ethical hacking,” is a systematic process of evaluating the security of an organization’s network infrastructure. The primary objective is to identify vulnerabilities, assess potential attack vectors, and recommend measures to strengthen the network’s defenses. Ethical hackers, or penetration testers, conduct these assessments with explicit authorization and adhere to strict ethical guidelines.
Significance of Network Penetration Testing:
- Identifying Weaknesses: Network penetration tests help organizations identify vulnerabilities and weaknesses within their network infrastructure, including misconfigurations, software flaws, and security gaps.
- Assessing Real-World Risk: By simulating real-world cyberattacks, these tests provide insights into the actual risk an organization faces, allowing for more effective risk management and mitigation.
- Regulatory Compliance: Many industries have regulatory requirements governing network security. Network penetration testing helps organizations demonstrate compliance with these regulations.
- Continuous Improvement: Regular testing fosters a culture of continuous improvement in cybersecurity, enabling organizations to stay ahead of emerging threats.
Methodologies of Network Penetration Testing:
- Pre-Engagement Phase: This phase involves defining the scope, objectives, and rules of engagement for the penetration test. It also includes obtaining the necessary permissions and agreements from stakeholders.
- Reconnaissance: Testers gather information about the target network, including IP ranges, subdomains, and network architecture. Tools like Nmap and OSINT techniques are often used during this phase.
- Scanning and Enumeration: In this step, testers identify open ports, services, and vulnerabilities within the network. They may use tools like Nessus or OpenVAS for automated scanning.
- Vulnerability Analysis: Vulnerabilities discovered during scanning are analyzed to assess their potential impact and likelihood of exploitation. Testers prioritize vulnerabilities based on risk.
- Exploitation: Testers attempt to exploit identified vulnerabilities to gain unauthorized access to network resources. This phase requires ethical hacking skills and knowledge of various attack techniques.
- Post-Exploitation: Once access is gained, testers may investigate the extent of compromise, escalate privileges, and move laterally through the network to discover additional vulnerabilities.
- Reporting and Remediation: The results of the penetration test are documented in a detailed report, including findings, potential risks, and recommendations for remediation. This report guides the organization’s efforts to improve network security.
Examples and Scenarios:
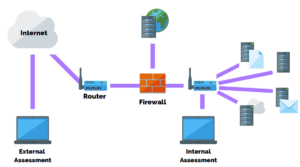
- External Network Penetration Testing: Assessing the security of the network from an external perspective, mimicking the actions of an external attacker trying to gain access.
- Internal Network Penetration Testing: Focusing on the security of internal network segments, including testing against insider threats and lateral movement.
- Wireless Network Penetration Testing: Evaluating the security of wireless networks, identifying weak encryption, rogue access points, and potential vulnerabilities.
Network penetration testing is an invaluable tool for safeguarding your organization’s digital backbone. By systematically identifying vulnerabilities and weaknesses within your network infrastructure, you can enhance security, mitigate risks, and fortify your defenses against evolving cyber threats. Ethical hackers who conduct these tests are essential allies in maintaining the integrity and resilience of your network. In the dynamic landscape of cybersecurity, network penetration testing is a proactive and strategic approach to securing your digital assets.